
Spot a Phishy Email
Just because you have security software on your computer or phone doesn’t mean you’re free from phishing emails. That’s what makes phishing so devious. These emails can arrive looking so convincing and seemingly harmless that users don’t pause to question it before they click a link or open an attachment – and by then it’s too late.
Picture this:
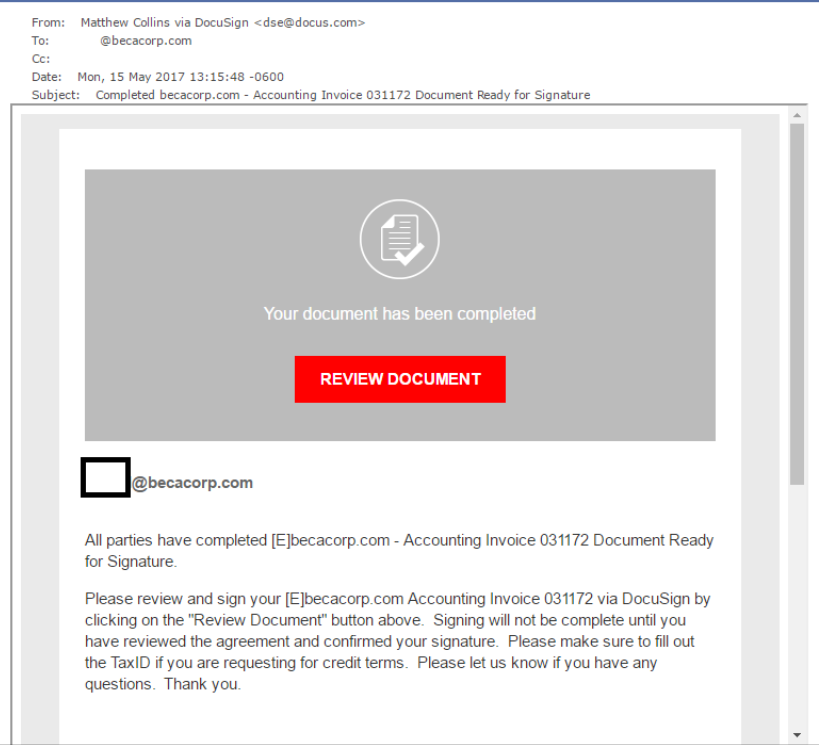
You’re checking your email first thing in the morning when you notice one from DocuSign stating that you need to sign a document for your accounting department. It’s early and the email looks legit without thinking, you click the embedded link or attachment. Without even knowing it, you fell victim to a phishing email.
The image below is one that actually made it into my inbox. Can you spot some of the phishing signs?
You’re probably thinking:“I’m way too busy in my day to stop and scan every single email that comes into my inbox.”
That’s understandable, but there are a few fast things you can check for that take seconds saving you from falling victim to a phishing scam.
Start training yourself now to look for these signs to spot a phishy email. It will become second nature and soon you won’t even realize that you do it. Follow these steps in order each time an email comes into your inbox.
1. Was I expecting this?
The easiest and quickest thing you can do for every email that comes into your inbox is to just ask yourself – “was I expecting this?”If the answer is yes, then it is probably safe. If the answer is no, then you may need to look a little closer at the email before taking action.
Let’s look back at that DocuSign email from above. When I first saw that email, I needed to take just a second to pause before clicking the link and ask myself – “Has the accounting department ever sent me a Docusign link before?” And, “Is this the way they normally do it?” And, “Was I expecting this important document?” All of these questions took just seconds of my time, but they helped make me instantly alert.
2. Name Check
Look at the “from” address of the email. A lot of phishing emails use a sender’s email address that is like, but not identical to, a company’s official email address. Name spoofing is done in several ways, but the most common ways include:
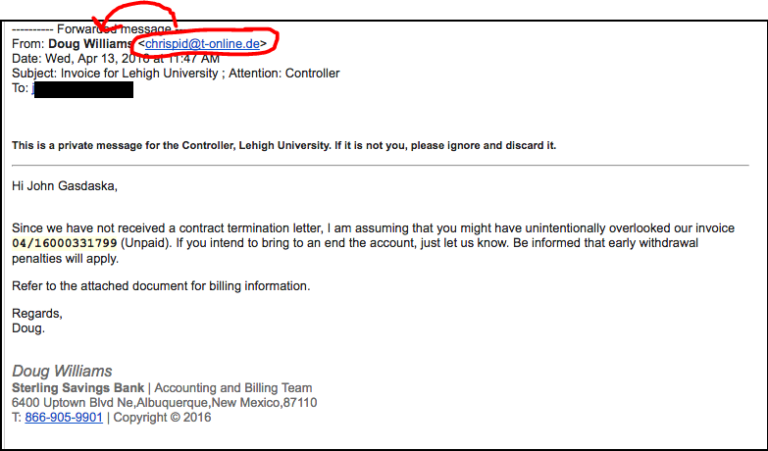
- Changing the name of the sender so that it doesn’t match the email address. Look at the example below. The name on the email address DOES NOT match the sender’s name.
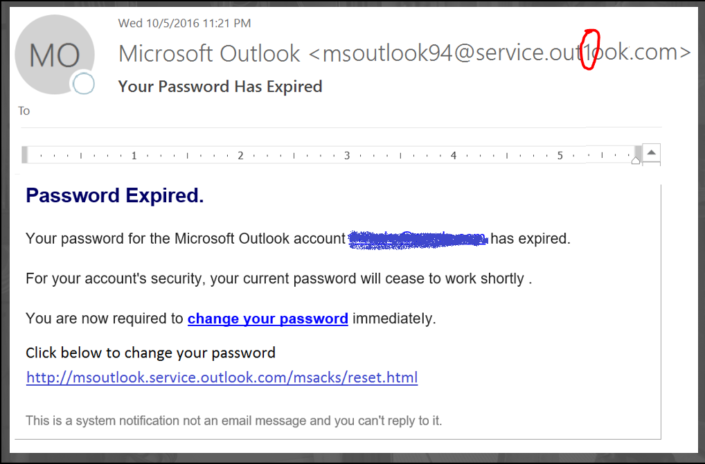
- Using characters that are similar to actual letters. For example, they may use a Greek letter or a number in the email address that looks similar to a Latin letter.
- Creating a fake sender email address that references a normally trustworthy institution.
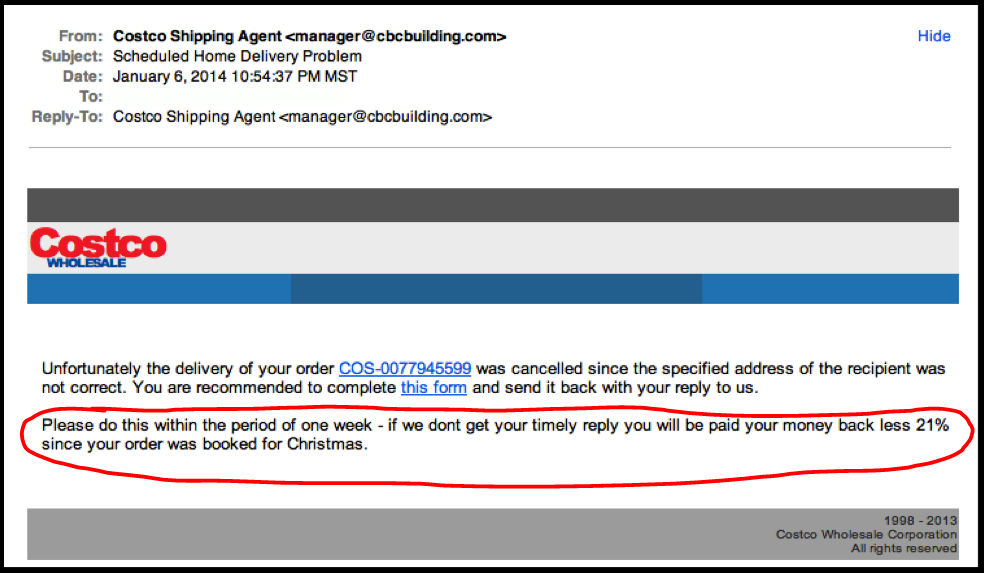
3. Is the email urgent?
Most phishing emails almost always sound desperate. They might be claiming that your account will be closed in 24 hours or maybe that an urgent request is needed. Always think twice before clicking that link or opening the attachment.
4. Look but don’t touch
If there are links in the email, always hover over them before clicking. The actual hyperlink should appear when you hover. If that hyperlink is not the same as the link they are asking you to click, DO NOT click!!
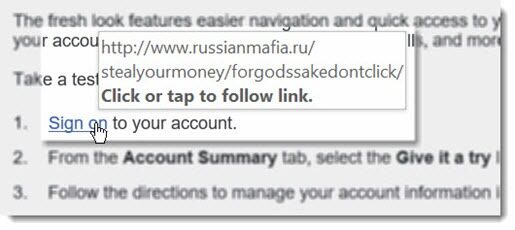
Make sure you look closely. Sometimes the link may look very convincing (unlike the example above), but it is just slightly different from the actual website address.
If you think it might be real but are still hesitant to click, better safe than sorry!! Just go directly to the company’s website and log into your account rather than going through a link in an email.
5. Check for spelling mistakes
This one is at the last of the list for a reason. Sometimes it can be a tell-tale sign of a phishing email. However, cyber criminals are getting smarter and their emails are starting to look more and more realistic. Do not only rely on bad spelling as a sign of a dangerous email.
So let’s go back to the DocuSign example from the beginning of this post. This is a real email that came into my inbox last spring. If I wasn’t paying attention, I could have ended up having a very bad day. Now that we’ve covered some of the top signs to look for, let’s highlight those in the same DocuSign email.
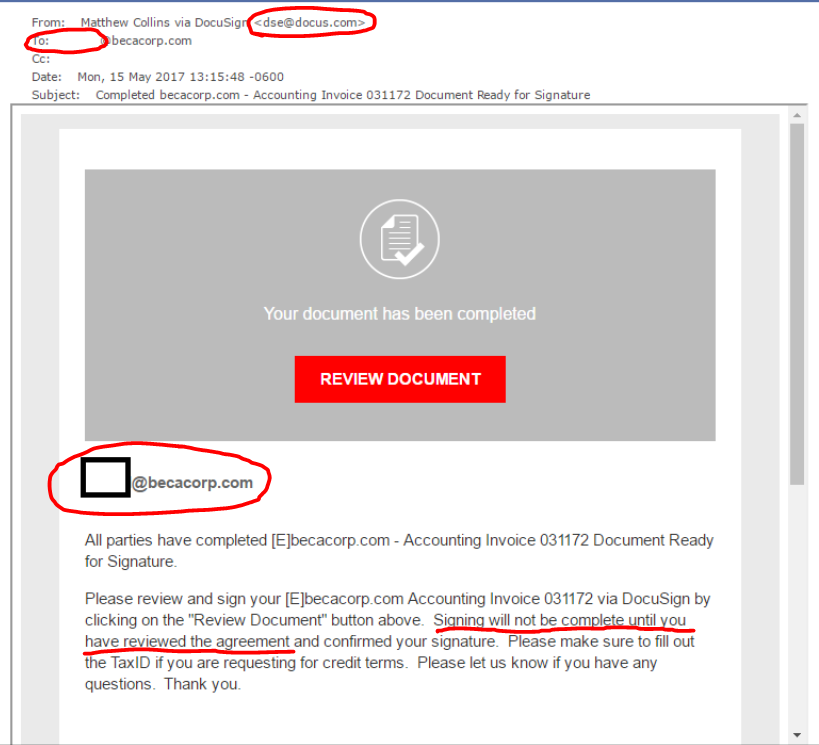
- Was I expecting this document? No.
- Name check. The name and email address don’t match up. Especially because DocuSign’s normal email format is firstname.lastname@docusign.com.
- Is the email urgent? Somewhat. They are stating that the signing won’t be completed until I click the link to review the document.
- Look but don’t touch. Hovering over the “Review Document” link showed a hyperlink that was similar to, but not the same as, DocuSign’s website.
- Spelling mistakes. A perfect example of why this is at the end of the list. There aren’t many. The format and grammar is a little strange, but nothing blaring.
Other important signs: This email does not look like DocuSign’s normal emails which are usually dark blue, not red. Also, my name is nowhere on this email. Instead, it left a blank spot where the beginning of my email should have been.
So what should you do if you spot a phishy email? Every company has a different procedure, but there are a few good practices that you can follow no matter what:
- Do not reply.
- Notify your IT department. Give them a call and let them know that you got a suspicious email. They will probably ask that you forward the email to them so that they can confirm, and determine if anyone else got the same email.
- Don’t forward it along to your employees. Even if you have the best of intentions and are letting your employees know, “If you get this email don’t click on it”, there is always that one employee who won’t bother to read your note and instead just see an email from you and click the link right away. Whoops.
- Delete the email. Once you have notified the correct personnel, go ahead and permanently delete the email.
Want to learn more about email security best practices? Get in touch with our experts.
Share the IT Brain Power
More from the BECA Blog



